5:17 p.m., Oct. 6, 2015–News reports of cyberattacks have become frighteningly frequent.
In June 2015, it was reported that a data breach of the U.S. Office of Personnel Management affected some 4 million federal employees.
In August, updated information showed that the number was actually closer to 21.5 million and included not only federal employees but also civilians.
In September, USA Today reported that cyberattackers had successfully compromised the security of U.S. Department of Energy computer systems more than 150 times between 2010 and 2014.
And on Oct. 2, just one day into National Cybersecurity Month, it was reported that a hacker had acquired the records of 15 million T-Mobile customers and people who had applied for credit through Experian.
“Thousands of cyberattacks are launched daily around the globe by people attempting to capture and use or sell critical information,” says Starnes Walker, founding director of the University of Delaware Cybersecurity Initiative. “Attackers can threaten our national security, steal years of experimental research data, gain access to the power grid or tamper with our financial markets.”
The Cybersecurity Initiative was established at UD in 2014 as a partnership among the state, the University, federal agencies and the private sector to address this problem — which costs billions of dollars a year — through education, workforce training and research and development.
Babatunde Ogunnaike, dean of the College of Engineering, believes that a holistic and systematic approach is essential for a cybersecurity program to have a lasting positive impact on society.
“Such an approach must include strategic organization of the basic components of the cyberlandscape and appropriate alignment of program activities with these components,” he says. “The methodology we’ve developed provides a universal view that is independent of specific applications, industries and fields.”
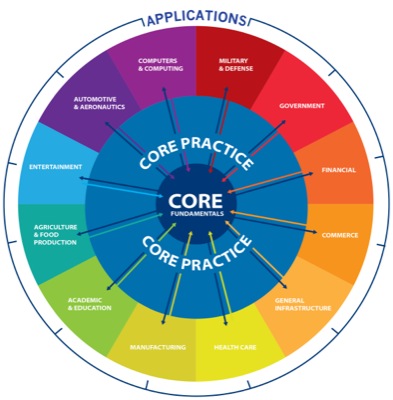
Bringing order to the cyberlandscape
At the center of this view (shown in this illustration) are core fundamentals, or the elements upon which cybersystems are built, including hardware, architecture, networks, platforms, software, software engineering, systems, algorithms and computing theory.
“These elements comprise the core of what enables a wide variety of computer applications,” says Ogunnaike. “All applications, regardless of complexity and importance, have these elements in common.”
The second component, core practice, comprises the work of the typical IT department of every organization: hardware and software selection and installation, application designs, networking, systems integration, systems management, troubleshooting and so on.
Ogunnaike explains that all application industries and categories, regardless of specific activities, rely on such practitioners for the implementation, operation and support of their respective systems.
Finally, applications include the disciplines and industries that use computing for daily functions. These cover virtually every aspect of modern life, from health care, manufacturing, entertainment and food production to defense, financial markets, commerce and civil infrastructure.
“It would be easy, but ultimately ineffective, to focus only on these application areas,” Ogunnaike says, “but they are on the outer ring in our organizational scheme because the work done in the core areas of fundamentals and practice is valuable across applications.”
Feeding the pipeline through education programs
In 2014, Cisco reported an estimated worldwide shortage of more than a million security professionals.
To help meet the need for experts in this rapidly growing field, UD is now offering a minor in cybersecurity, as well as two master’s degree options, one on campus and the other online.
The minor, which is open to all undergraduate majors at UD, provides students with the opportunity to infuse cybersecurity fundamentals into other degree programs.
The master’s program is structured to provide professionals with advanced training in the field. Unlike programs focused solely on IT security, UD’s cybersecurity master’s emphasizes design of secure software and systems, security analytics and secure business systems.
“Students with a traditional background in engineering, computer science, information systems or a related field will gain strong security skills through the master’s programs,” says Ken Barner, chair of the Department of Electrical and Computer Engineering.
Kick-starting the research engine
An internal grant program has also been launched at UD, supported by the Office of the Provost, to support multidisciplinary research projects. Faculty are encouraged to submit proposals in all aspects of cybersecurity, with an emphasis on curriculum development and financial, managerial and behavioral topics.
“Preference will be given to projects that involve interdisciplinary collaboration, technology-engineering partnerships and/or industry connections,” Walker says. “We want to expand participation in the Cybersecurity Initiative, and we encourage faculty from all seven UD colleges to generate ideas that we can consider funding.”
“The field is wide open,” he adds, “with possible areas of study ranging from social engineering, cyberlaw, risk management and ethics to cloud security, cryptography, data mining and IT forensics.”
Proposals are due Nov. 8, awards will be announced Jan. 8, 2016, and funding will be available Feb. 1, 2016.
Click here for complete guidelines on proposal submission.
About the Cybersecurity Initiative
The mission of the University of Delaware Cybersecurity Initiative (UD CSI) is to establish UD as a center of excellence in cybersecurity that encompasses research, education, workforce training and development and promotes partnerships among the government, private and academic communities. UD CSI’s strategic focus is to serve as the cybersecurity hub for corporate America.
UD CSI is expanding the pipeline of skilled cybersecurity workers that our nation needs now and in the future; producing unbiased research and standard protocols for optimal security so that every type and size of business can protect itself; and helping individuals and businesses adopt best practices to handle this ever-growing threat.
Delaware is the ideal location for a cybersecurity hub. Situated halfway between New York City and Washington, D.C., the University can help make the essential connections between the corporate community and the military and intelligence community. Also, Delaware is the legal home of more than 1 million corporations and a highly regarded court system, so legal questions in the evolving field of corporate cybersecurity will be adjudicated in Delaware. Finally, UD already has expertise in a number of critical fields, including computer engineering, computer science, corporate law and public policy.
UD CSI is developing programs through relationships with a broad array of partners, including government agencies, private industry and other academic institutions.
Visit the website for more information about the initiative.
Article by Diane Kukich | Illustration by Joy Smoker